Cloud computing has evolved from a luxury to an absolute necessity in today’s fast-paced digital world. As your organisation grows, relying on a single cloud provider can quickly become a constraint, limiting your flexibility, negotiating power, and overall resilience. You might find yourself locked into one ecosystem, unable to adapt swiftly to changing demands or optimise costs effectively.
This is precisely where multi-cloud strategies come into their own, offering you the freedom to harness the best of multiple providers like AWS, Azure, and GCP.
In this blog, you’ll gain exclusive insight into how a dedicated Dev Team meticulously built a powerful, flexible, and secure multi-cloud migration tool from the ground up. We’ll walk you through the challenges, innovations, and key lessons that shaped this essential tool, designed to empower you to conquer multi-cloud complexities with confidence and ease.
1. What is a multi-cloud migration tool?
- A multi-cloud migration tool helps you move your apps, data, and services between different cloud providers like AWS, Azure, and Google Cloud. It makes switching or using multiple clouds easier by managing everything in one place. With this tool, you don’t have to learn each cloud’s system separately. It automates the process, reduces mistakes, and saves time. Using a multi-cloud migration tool gives you more flexibility, control, and helps avoid being stuck with just one cloud provider.
1.1 Key Features of the Tool
a. One-Click Migrations
- With One-Click Migrations, you can start a full migration just by pressing a button. It pulls from your Infrastructure as Code (IaC) templates and runs everything automatically. You don’t need to type commands or manage each step yourself. This saves time, reduces mistakes, and makes the whole process easier. It’s a fast, simple, and repeatable way to move your setup from one cloud environment to another without worrying about doing things manually.
b. Multi-Cloud Support
- The tool gives you Multi-Cloud Support, which means you can easily switch between AWS, Azure, and GCP. Instead of learning three different platforms, you just use one system that handles them all. This helps you manage resources across different cloud providers without extra work. It also gives you flexibility and helps prevent vendor lock-in, so you’re not stuck using just one cloud service forever.
c. Custom Module Support
- With Custom Module Support, you can upload your own Terraform modules or register ones built by your team. This means you don’t have to rely only on built-in tools—you can bring your own code and make it work with the system. This feature gives you more control, supports custom setups, and makes it easier to match your company’s specific needs during migrations or cloud builds.
d. Role-Based Access Control (RBAC)
- Role-Based Access Control (RBAC) lets you set granular permissions for every user. You control who can do what—some people might only view resources, while others can change things. This helps keep your cloud setup safe and prevents mistakes from people accessing things they shouldn’t. RBAC is especially helpful when working with teams because it keeps everyone in their lane while still allowing collaboration.
e. Dry Run and Validation Mode
- Dry Run and Validation Mode let you test your changes before they go live. You’ll see a complete diff preview, which shows exactly what will change in your setup. This helps you catch problems early and avoid breaking anything by accident. It’s like doing a practice run before committing. This feature gives you more confidence, improves accuracy, and makes your migrations safer and smoother.
2. Why You Need a Multi-Cloud Migration Tool
- You needed a multi-cloud migration tool because your clients started using AWS, Azure, and Google Cloud Platform (GCP) together. You quickly saw that most tools were either locked to one vendor, too complex to manage, or lacked the flexibility you required. By creating your own solution, you ensured smooth migration, better control, and consistent performance across platforms. This helped you avoid tool limitations and gave you the ability to support your clients’ growing multi-cloud strategies efficiently.
a. Granular control over infrastructure migration
- You needed granular control to manage each part of your infrastructure migration precisely. This meant being able to migrate individual workloads, set custom rules, and adjust configurations based on application-specific needs. Without this control, you risked performance issues or downtime. By having deep visibility and fine-tuned management, you could ensure every component moved safely, predictably, and efficiently, especially when working across different cloud platforms where standard migration behaviors often don’t fit your unique infrastructure requirements.
b. Support for multiple providers out of the box
- You couldn’t rely on a tool that favored one vendor. You needed native support for AWS, Azure, and GCP—right from the start. Switching tools or adding plugins for each cloud provider would slow you down and introduce compatibility risks. By supporting multiple providers out of the box, you simplified operations, reduced integration overhead, and gave yourself the freedom to adapt to changing client requirements. It also meant faster onboarding and easier scaling across cloud ecosystems.
c. Repeatability and automation
- To streamline migrations, you needed repeatability and automation. Manual steps not only wasted time but also increased the risk of errors and inconsistencies. By automating processes, such as resource provisioning, policy enforcement, and rollback, you ensured consistent results across environments. Repeatability meant you could reuse tested workflows, saving effort on future projects. This approach allowed you to scale migration efforts, reduce human intervention, and maintain high standards in performance and reliability every time you executed a migration.
d. Security and compliance are baked in
- You couldn’t afford to treat security and compliance as an afterthought. They had to be built into the tool from the beginning. With baked-in features like data encryption, access controls, and audit logging, you met regulatory standards while protecting sensitive information during migration. This approach also helped you respond confidently to compliance audits and ensured that client data stayed safe. Security-by-design minimizes vulnerabilities and aligns your migrations with industry best practices and legal obligations.
Summary:
- You realized that existing tools failed to deliver in one or more key areas—whether it was granular control, multi-cloud support, automation, or built-in security. Each shortcoming created risks and inefficiencies. To meet your standards and your clients’ expectations, you chose to build your own solution, tailored to handle complex migrations across diverse cloud environments effectively.
3. Core Goals
- Before writing a single line of code, you clearly defined what success meant. You focused on building a solution that was provider-agnostic, automated, scalable, secure, and developer-friendly. By setting these core goals up front, you ensured every decision aligned with your long-term vision, helping you deliver a tool that truly met your clients’ multi-cloud migration needs.
a. Provider-Agnostic Framework
- You committed to a provider-agnostic framework to avoid vendor lock-in and ensure seamless interoperability with AWS, Azure, and GCP. Through a modular approach, you enabled integration with various cloud services without needing to rewrite core logic. This architectural choice offered flexibility, portability, and future readiness, allowing your tool to adapt as cloud ecosystems evolve. It empowered you to deliver consistent experiences across environments and positioned your platform as a truly cloud-neutral migration solution.
b. Infrastructure as Code (IaC) Foundation
- By embracing an Infrastructure as Code (IaC) foundation, you ensured all migration tasks were automated, auditable, and rollback-safe. This methodology lets you define infrastructure in version-controlled files, eliminating manual errors and enabling repeatable deployments. IaC aligned your tool with DevOps best practices, offered enhanced traceability, and allowed for rapid infrastructure provisioning. It gave you both control and confidence in complex environments, making your migration processes resilient, scalable, and easier to manage over time.
c. Scalability
- You prioritized scalability to serve both startups and large enterprises without performance compromise. Your tool was architected to handle varying workloads, from small-scale test migrations to large, enterprise-wide transitions. You built for horizontal scaling, fault tolerance, and load optimization, ensuring consistent throughput regardless of size. This capability allowed you to meet evolving client demands while maintaining reliability. With scalability at the core, your solution became capable of supporting growth, volume, and complexity with equal proficiency.
d. Security and Compliance
- You embedded security and compliance into the design from day one, recognizing their non-negotiable importance. From identity and access management to data encryption, you implemented controls aligned with strict frameworks such as SOC 2 and HIPAA. This ensured your tool met industry and regulatory expectations while protecting sensitive assets during and after migration. By prioritizing compliance automation and audit-readiness, you reinforced trust and positioned your platform for adoption in regulated sectors with high security demands.
e. Developer-First Design
- You chose a developer-first design to make your tool intuitive and efficient for DevOps engineers. Rather than catering solely to architects, you focused on those executing real-world migrations. This meant clean UX, powerful CLIs, and documentation designed with empathy. By removing friction and reducing cognitive load, you improved adoption and productivity. Your developer-centric philosophy empowered engineers to work faster and with greater confidence, embedding your tool into their daily workflows and reinforcing its value in practical operations.
4. Choosing the Right Tech Stack
- When selecting your tech stack, you prioritized flexibility, strong integration support, and the ability for fast iteration. Your architecture required components that could adapt to evolving needs, work seamlessly across systems, and support rapid development cycles. By choosing proven, cloud-native technologies, you ensured your platform would be scalable, efficient, and future-ready from the ground up. Here’s what you went with:
a. Frontend – React.js
- You chose React.js for the frontend because it helps you build modern, interactive web pages using components. That means you can break your UI into smaller parts and reuse them easily. React also updates the screen quickly without reloading everything, making the experience smooth. It’s widely used, so there are tons of tutorials and support. By using React, you made your tool’s interface fast, user-friendly, and easy for other developers to understand and work with.
b. Backend API – Node.js + Express
- For your backend, you picked Node.js with Express to handle the server-side logic. Node.js is great for running JavaScript outside the browser, and Express helps you organize code and manage routes. This combo made it easier for you to build a fast, scalable, and REST-friendly API that connects the frontend to the backend smoothly. Since both use JavaScript, you only needed one language for the whole app, which saved time and boosted productivity.
c. Orchestration – Terraform
- You used Terraform for orchestration because it’s the leading tool for Infrastructure as Code (IaC). With Terraform, you write code to manage cloud resources like servers and databases instead of doing it manually. It helps you make changes safely, repeat tasks, and track everything. It works with AWS, Azure, and GCP, so it’s perfect for multi-cloud setups. This made your tool more automated, reliable, and easier to manage for both you and your users.
d. State Management – Remote S3 + DynamoDB
- You picked S3 and DynamoDB to manage state securely and reliably. When using tools like Terraform, you need a place to store the current setup of your infrastructure—this is called “state.” By saving it in S3, you made it shared and backed up, and with DynamoDB, you handled locking so two people don’t overwrite the same file at once. This setup kept your migrations safe, organized, and ready for teamwork in the cloud.
e. Authentication – Auth0
- You chose Auth0 for authentication because it made adding secure login easy. Auth0 supports OAuth2, Multi-Factor Authentication (MFA), and Single Sign-On (SSO)—all the tools needed to protect user accounts. It also handles password storage, login pages, and user sessions without much setup. With Auth0, you saved time and gave users a safe and simple way to access the tool. It helped you meet security standards while keeping the developer experience smooth.
f. CI/CD – GitHub Actions + Argo CD
- You used GitHub Actions and Argo CD to handle CI/CD, which means Continuous Integration and Continuous Deployment. GitHub Actions helps you automate testing and building your code when you push changes. Argo CD makes it easy to deploy updates to the cloud using declarative configuration. This combo gave you a cloud-native, fast, and reliable pipeline, so you could release updates quickly and safely. It also ensured your code was always in sync with your infrastructure.
g. Logging/Monitoring – ELK Stack
- You picked the ELK Stack—Elasticsearch, Logstash, and Kibana—for logging and monitoring. It helped you see what’s happening in your tool in real time, by collecting logs, analyzing them, and displaying them in visual dashboards. If something breaks or slows down, you can find the issue fast. This setup gave you transparency, made debugging easier, and helped you keep things running smoothly. It also ensured your team could monitor performance and fix problems before users noticed.
| Component | Technology | Why We Chose It |
|---|---|---|
| Frontend | React.js | Modern, component-based UI |
| Backend API | Node.js + Express | Fast, scalable, REST-friendly |
| Orchestration | Terraform | Best-in-class IaC tool |
| State Mgmt | Remote S3 + DynamoDB | For secure and shared state |
| Authentication | Auth0 | OAuth2, MFA, SSO capabilities |
| CI/CD | GitHub Actions + Argo CD | Cloud-native and declarative |
| Logging/Monitoring | ELK Stack | Real-time visibility into operations |
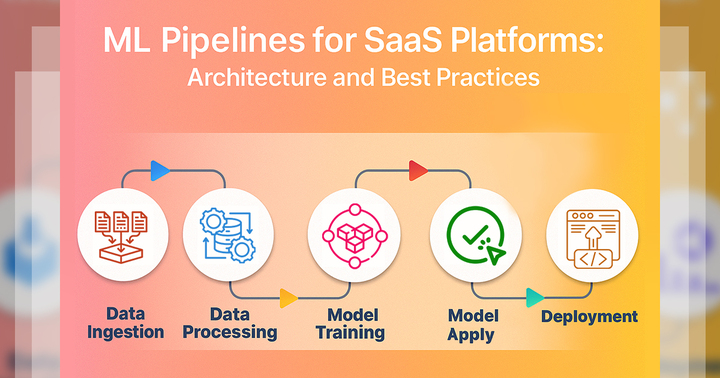
5. Architecture Overview
- Your tool uses a microservices-based architecture, which means it’s made of small parts that each do one job well. These parts work together to manage cloud migrations across AWS, Azure, and GCP. Each service handles things like the user interface, API calls, Terraform tasks, and logging, making the system more flexible, scalable, and easier to manage. Here’s a simplified view:
a. Frontend UI – User input and real-time status
- The Frontend UI is where you interact with the tool. It lets you enter commands, set options, and see real-time updates on your migration. Built with modern web tech, it’s made to be fast and easy to use. You don’t need to know the technical details underneath—just use the interface to manage cloud operations smoothly. This part of the system helps you control the process and watch progress live as it happens.
b. API Layer – Receives requests, triggers the orchestrator
- The API Layer is the middleman between the user and the tool’s logic. When you press a button or start a migration, the API receives the request and passes it to the orchestrator. It makes sure your input is handled correctly and that the right services are triggered. This layer keeps things organized, handles security checks, and ensures that commands get sent to the right place at the right time without delays.
c. Orchestrator Service – Manages Terraform workflows
- The Orchestrator Service is like the tool’s brain. It controls Terraform workflows, which means it runs the scripts that build or change cloud resources. When you start a job, this service figures out what steps to take and when to take them. It also manages errors, tracks progress, and makes sure everything runs in the right order. This helps you automate complex tasks without having to do them one by one.
d. Provider Modules – Separate logic for AWS, Azure, GCP
- You use Provider Modules to keep the code for AWS, Azure, and GCP separate. Each cloud has its own tools and rules, so this setup lets you write special instructions for each one. If you need to add a new service or provider later, you don’t have to change the whole system—just update one module. This makes your tool more flexible, organized, and ready to grow as you add more features.
e. State Store – Centralized in S3 and DynamoDB
- The State Store keeps track of everything your tool builds or changes. You store this information in S3 and DynamoDB so it’s safe, shared, and always up to date. If you or your team ever need to undo something or check what’s been done, you can look here. This makes your setup more reliable, supports team collaboration, and prevents mistakes during migration by keeping track of the current state of your infrastructure.
f. Audit Logs – Sent to Elasticsearch for inspection
- Audit Logs record every action your tool takes—like who did what and when. You send these logs to Elasticsearch, which makes them searchable and easy to review. If something goes wrong or you need to prove you followed rules (like for compliance checks), you can inspect these logs. This helps you stay secure, transparent, and ready to explain any changes made during a cloud migration, especially in serious industries like healthcare or finance.
Summary:
- You abstract each cloud provider’s setup into separate modules, which means you group the logic for AWS, Azure, and GCP into their own blocks. This makes it easy for you to scale, update, or add new cloud services without changing everything. It keeps your tool more organized, flexible, and ready for future growth.
6. Challenges We Faced
- Building a tool like this came with real challenges. You had to deal with cloud differences, fix issues with Terraform state, protect secrets, and build smart error handling. It wasn’t always easy, but facing these problems helped you create a stronger, more reliable tool. Each challenge pushed you to make smarter, more secure, and scalable choices.
a. Cloud Provider Differences
- Each cloud provider has its own unique ways of doing things, which made building the tool tricky. For example, AWS uses VPCs for networking, while Azure uses VNets. Their IAM policies (which control access) are set up very differently, and their APIs behave in different ways, including limits like throttling. You had to learn these differences and make the tool work smoothly across all clouds without breaking anything.
b. Terraform State Conflicts
- When multiple people or processes try to change infrastructure at the same time, you risk state conflicts—where changes clash or overwrite each other. To fix this, you had to build state locking and conflict detection into the tool. This means the system knows when something is already being changed and prevents mistakes. This made your tool safer and more reliable when many users work together or when multiple tasks run simultaneously.
c. Secrets Management
- Handling secrets like passwords or API keys was a big challenge. You didn’t want to store sensitive information directly in the code because that’s unsafe. So, you integrated with Vault, a secure system that stores secrets safely. This way, your tool can access credentials when needed without risking exposure. Using Vault improved your tool’s security, prevented leaks, and made managing secret information easier and safer for everyone.
d. Error Recovery and Retry Logic
- Migrating infrastructure is risky because errors can break things. Your tool had to handle failures smartly by adding error recovery and retry logic. This means if something goes wrong, the tool tries again or safely rolls back to the last stable state. It prevents disasters and keeps systems running smoothly. By building this, you made sure your migration tool could fix problems automatically and protect your cloud environments during complex changes.
- Each cloud provider’s infrastructure is abstracted into modules, making it easy to scale or add new services.
7. Security Considerations
- From the start, you made security a top priority. You didn’t wait until later—you planned for it from day one. That means every part of your tool was built with safety in mind, from how you handle secrets to how users log in. This helped you protect data, follow compliance rules, and build trust with users.
a. All communication is TLS-encrypted
- You protect all data sent between systems using TLS encryption. This means no one can read or change what’s being sent, even if they try to spy on the network. Whether it’s user info or cloud commands, TLS keeps it safe. By using this secure communication method, you protect against hackers, prevent data leaks, and make sure everything sent between parts of your tool stays private and tamper-proof.
b. OAuth2 + MFA for all users
- You use OAuth2 for login, which is a strong and secure way to prove who you are. On top of that, you add Multi-Factor Authentication (MFA), so even if someone steals a password, they can’t get in without the second step—like a phone code. This double layer makes it much harder for attackers to break in and keeps your user accounts safe and locked down.
c. Least privilege principle with RBAC
- You follow the least privilege rule using Role-Based Access Control (RBAC). That means each person only gets access to what they actually need—nothing more. For example, a developer might view things but not delete them. This keeps your tool secure by lowering the risk of accidents or misuse. It also helps protect sensitive cloud resources and ensures people don’t have more power than necessary.
d. Secrets stored in Vault with TTLs and audit logs
- You store sensitive data like passwords and API keys in Vault, not in your code. Vault gives each secret a Time To Live (TTL), so it expires if not used, which limits risk. Plus, audit logs track who accessed what and when. This setup makes your tool much more secure, and it keeps you compliant with important safety standards and privacy rules.
e. Terraform plans validated before execution
- Before you run any changes in the cloud, your tool shows a Terraform plan preview. This lets you check what’s about to happen and spot mistakes. You can fix issues before anything goes live. It’s like seeing a “preview” before making edits permanent. This step helps you avoid costly errors, keeps infrastructure safe, and gives you more control over every change.
Summary:
- You added audit logs to track every user action—like who did what, when, and where. This helps you keep your tool secure and accountable. If something goes wrong, you can quickly find out what happened. These logs also help with compliance and make sure everyone is using the system the right way.
8. Testing and QA
- For your multi-cloud migration tool, you used a layered testing strategy to make sure everything works smoothly. You tested small parts with unit tests, checked connections with integration tests, ran full end-to-end tests, scanned for security issues, and performed load tests to see how it handles pressure. This strategy keeps your tool reliable, secure, and ready for real-world use.
a. Unit Tests
- You use unit tests to check if each small part of your code, like a function or module, works correctly on its own. These tests help you catch bugs early before they spread. By testing one piece at a time, you make sure your tool’s logic is reliable. Unit tests are fast to run and super useful when you’re writing new features or changing old ones because they tell you what breaks.
b. Integration Tests
- With integration tests, you check how different parts of your tool work together—especially when creating cloud resources like servers or networks. These tests help you make sure that the system behaves correctly when pieces interact. If something breaks when modules connect, integration tests will catch it. They’re important for making sure your tool works in real-world setups where different systems must communicate and function as one.
c. End-to-End Tests
- End-to-End tests make sure the full migration process works from beginning to end, just like a real user would experience it. You test everything—from clicking “start” to finishing the cloud migration. These tests show you if the whole system is behaving as expected. They’re slower than unit tests, but they’re super useful for catching workflow errors or things that only break when the whole tool is running together.
d. Security Scans
- You run security scans to look for open ports, leaked secrets, or misconfigurations in your setup. These scans help you protect your system from hackers and other security risks. If something’s exposed or unsafe, the scan will let you know so you can fix it fast. Running regular scans keeps your tool more secure and makes sure you’re not missing anything dangerous or out of place.
e. Load Tests
- You use load tests to see how your tool performs when lots of people are using it at once. This helps you check if it’s fast, stable, and able to handle heavy usage. If the tool slows down, crashes, or gets stuck, these tests show you where the problem is. They help you build a system that works well not just in tests—but in real-life traffic.
| Test Type | Purpose |
|---|---|
| Unit Tests | Validate module logic |
| Integration Tests | Test cloud resource provisioning |
| End-to-End Tests | Validate the full migration workflow |
| Security Scans | Check for open ports, secrets, misconfigs |
| Load Tests | Ensure performance under heavy usage |
9. Deployment and CI/CD Integration
- For your multi-cloud migration tool, you use a smart CI/CD pipeline to deploy updates safely. You run GitHub Actions for testing and building, use Argo CD to handle Kubernetes deployments, and manage setup with Helm Charts. Every change first goes to a preview environment, so you can fix issues before pushing to production, keeping everything safe and stable.
a. GitHub Actions for testing, linting, and Docker builds
- You use GitHub Actions to automate tasks like testing your code, checking for style errors (linting), and creating Docker builds. Every time you make a change, these steps run automatically. This helps you catch mistakes early and keeps your code clean and reliable. It also saves time by doing the boring work for you. GitHub Actions makes sure your tool is always in good shape before it moves to the next stage.
b. Argo CD for Kubernetes-based deployment
- With Argo CD, you deploy your tool to Kubernetes clusters in a smart and safe way. It constantly checks if what’s running matches your code, and if not, it fixes it. This means your tool is always up-to-date and consistent. Argo CD uses a declarative approach, so you define how things should look, and it takes care of making it happen. It gives you control, speed, and fewer mistakes during deployment.
c. Helm Charts for infrastructure configuration
- You use Helm Charts to manage and install your infrastructure in a simple, repeatable way. Think of Helm like a package manager for Kubernetes—it bundles everything your app needs. Instead of writing everything from scratch, you use these charts to quickly set up databases, services, and settings. Helm helps you configure, organize, and automate cloud resources easily. It’s great for teams because it makes deployments more consistent and less error-prone.
Summary:
- Before anything new goes live, you test it in a preview environment. This is a safe space that looks like the real thing, where you can spot bugs and fix issues. Only after everything works perfectly does the change go to production, where real users will see it. This step protects you from breaking things and keeps your tool safe, stable, and user-ready.
10. Real-World Use Cases
- You can use a multi-cloud migration tool in many real-world situations. Whether you’re saving money, improving reliability, or growing your business, this tool gives you the flexibility to move between cloud providers like AWS, Azure, and GCP. It helps you handle challenges with costs, scaling, and disaster recovery—all with less stress and more control.
a. SaaS Startup Scaling Beyond AWS
- Imagine you’re running a SaaS startup and want to try Azure for better pricing or features. With this tool, you can easily copy your environment from AWS to Azure without starting from scratch. It helps you test everything first, so you know it works before switching. That means no big surprises. You get flexibility, speed, and a chance to grow your business across multiple cloud platforms—all without wasting time or resources.
b. Enterprise Cloud Cost Optimization
- If you’re part of a big enterprise, cloud bills can get really high. This tool helps you move your workloads between different providers like AWS, Azure, and GCP. By doing that, you can pick the cheapest option for each task. One company saved 30% just by using it smartly. So you’re not locked in, and you stay in control of your costs while keeping performance and reliability strong.
c. Disaster Recovery Planning
- Disasters can hit at any time—servers crash, data gets lost, or something just goes wrong. With this tool, you can set up a backup environment in another cloud like GCP or Azure. That way, if AWS goes down, your systems still run somewhere else. It’s a smart way to protect your business. This is called disaster recovery, and it gives you peace of mind when things get risky.
11. What You Learned
- When you develop a multi-cloud migration tool, you learn important lessons. You see that Terraform is powerful but needs careful state management. A modular design helps your tool grow easily. Clear documentation makes using the tool simple. Most importantly, security-first thinking is key and must be part of every step to keep everything safe and reliable. Here are the big takeaways:
a. Terraform is powerful but needs careful state handling
- You learned that Terraform is a strong tool to manage cloud resources, but you must be careful with its state files. If multiple people change the state at the same time, it can cause conflicts and errors. So, you need to use techniques like state locking to keep everything safe and consistent. Handling state properly is crucial to avoid problems and make migrations smooth.
b. Modular design is key for scalability
- You realized that building your tool with a modular design is super important. Breaking your code into separate, reusable parts lets you scale easily. You can add new cloud providers or features without starting over. Modules make your tool more flexible, easier to manage, and faster to update. This design helps your tool grow with your needs without getting messy or complicated.
c. Documentation matters. Every module, API, and workflow needs clear docs
- You understood that clear documentation is essential for success. Every part of your tool—modules, APIs, and workflows—needs easy-to-understand instructions. Good docs help users and developers know how to use and fix the tool without confusion. Without proper documentation, even the best tools become hard to maintain and use. Writing clear docs saves time and avoids mistakes.
d. Security-first thinking must be embedded at every layer
- You learned that security can’t be an afterthought; it has to be built into every part of your tool. From how users log in, to how data is stored and transmitted, you must protect everything. This mindset helps prevent breaches, keeps user data safe, and meets important compliance rules. Thinking about security from the start keeps your tool trustworthy and strong against attacks.
12. Future Roadmap
- For the future roadmap of your multi-cloud migration tool, you’re planning to add cool new features. You’ll support more clouds like OCI and IBM Cloud, use AI to give smart migration tips, build modules with an easy drag-and-drop UI, and include policy-as-code tools like OPA to keep everything secure and compliant. These updates will make your tool even more powerful and user-friendly.
a. Support for OCI and IBM Cloud
- You will soon be able to use the tool with more cloud providers like Oracle Cloud Infrastructure (OCI) and IBM Cloud. This means you get even more choices and flexibility to move your apps and data. Expanding support helps you avoid being stuck with just a few clouds, so you can pick the best one for your needs and grow your multi-cloud strategy smoothly.
b. AI-based migration recommendations
- The tool will use artificial intelligence (AI) to give you smart suggestions during migration. It can analyze your setup and recommend the best ways to move resources faster and safer. This helps you avoid common mistakes and saves time by guiding you through complex decisions. With AI, you get a helpful assistant that makes migration easier and more efficient, even if you’re new to cloud migrations.
c. Full drag-and-drop UI for module design
- You’ll get a new drag-and-drop user interface (UI) to build your migration modules visually. Instead of writing lots of code, you can simply drag pieces where you want them. This makes designing cloud infrastructure easier and faster, especially if you don’t like coding. The intuitive UI helps you focus on your goals and speeds up creating or changing your migration workflows with fewer errors.
d. Policy-as-code integration (e.g., OPA)
- The tool will support policy-as-code frameworks like Open Policy Agent (OPA). This means you can write and enforce rules automatically—like who can do what or what security standards must be followed. Integrating policies as code helps you keep your cloud environments secure and compliant without manual checks. It gives you better control and confidence that everything meets your company’s standards throughout the migration process.
Conclusion
- Building this multi-cloud migration tool was far more than a mere technical endeavour; it was a strategic investment that transformed how you and your clients navigate the cloud landscape. You’ve gained resilience by minimizing downtime and risks, flexibility by effortlessly switching between AWS, Azure, and GCP, and efficiency by automating complex migrations with precision. This tool doesn’t just solve problems — it empowers you to innovate boldly and adapt swiftly in an ever-changing digital world.
- If you’re grappling with the challenges of multi-cloud complexity, take this as both inspiration and a clear blueprint for success. With the right approach, tools, and mindset, you too can unlock seamless cloud migration, optimise costs, and strengthen security. Your journey to mastering multi-cloud begins here — with confidence, clarity, and cutting-edge technology working for you every step of the way.
FAQs
Q1: Can I use this tool without Terraform experience?
- A: Yes, you can! The tool’s user interface (UI) hides the complex Terraform commands, so you don’t need to know how to write them. But if you’re an advanced user, you can upload your own raw Terraform modules written in HCL (HashiCorp Configuration Language). This makes the tool easy for beginners but flexible enough for experts to customise their migrations.
Q2: Is it open source?
- A: Not yet. Right now, the tool isn’t open source, meaning the code isn’t publicly available for anyone to change or use freely. However, the team is looking into different licenses and ways to involve the community. This means in the future, you might be able to contribute or access the tool more openly, depending on the decisions made.
Q3: How do you handle credentials for each cloud provider?
- A: The tool uses Vault to securely store all your cloud credentials. It also creates short-lived access tokens that expire quickly to reduce risks. Plus, it applies strict Role-Based Access Control (RBAC) rules, so only the right people can access sensitive information. This setup keeps your secrets safe while letting you connect to different cloud providers without exposing passwords or keys.
Q4: Does it support hybrid cloud environments?
- A: Yes, it does! Besides working with public clouds like AWS, Azure, and GCP, the tool supports hybrid cloud setups where you combine on-premises data centres with the cloud. It can connect your local servers to the cloud using secure methods like VPN or Direct Connect, so you can manage and migrate infrastructure across both environments seamlessly.
Q5: Can I extend it for Kubernetes workloads?
- A: Absolutely! You can use the tool to migrate Kubernetes workloads running on platforms like EKS (AWS), AKS (Azure), and GKE (Google Cloud). It supports managing these clusters using Helm charts and Terraform, making it easier for you to move complex containerised applications between clouds. This means your Kubernetes setups are fully supported and flexible across multiple cloud providers.